Checking which clients ips are accessing your Azure Web App when you are running Windows is quite straightforward, but when you have linux it isn’t. Unless you are logging the IP addresses within your Web App implementation finding the IP of whose accessing the Web App isn’t trivial.
Recently we had a tenant which was target of a DDoS attempt from a China network, and we needed to block the IP, so we did the following (this requires a downtime of the Azure Web App):
- Login into your Azure Portal and open the Web App
- Go into Networking and click on Access Restriction
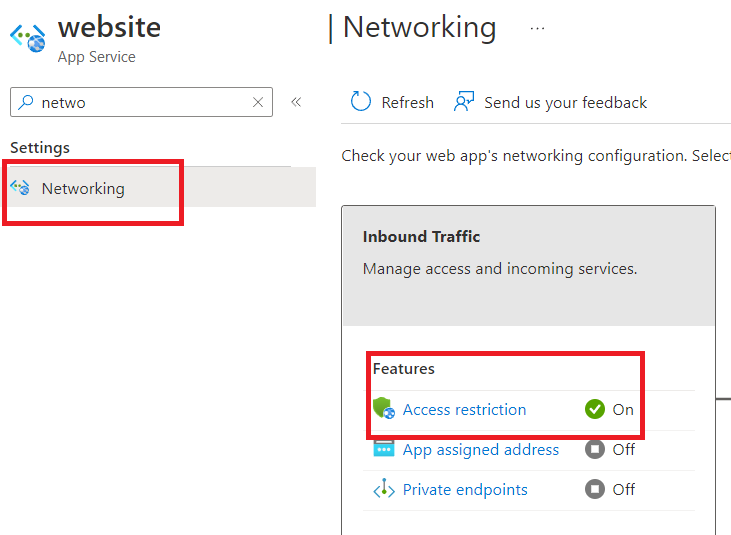
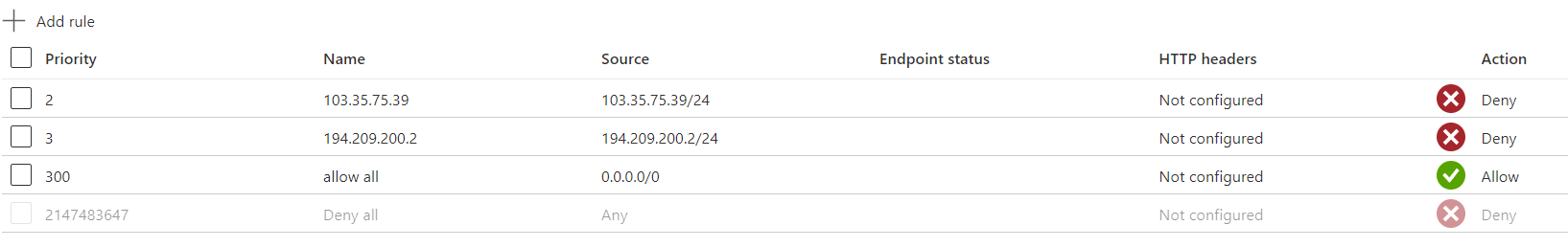
- If you’ve never added a rule then you’ll have something like a single entry with a very high priority allowing all traffic
- As soon as you add a new rule that existing “allow all” rule will change to “deny all”, which is actually what we want to find the clients’ ip addresses
- Add a new entry where you only allow your ip address with /24 at the end.This will deny access to all other IPs
- Wait for about 5 mins (this is 5 mins of downtime to everyone except your IP)
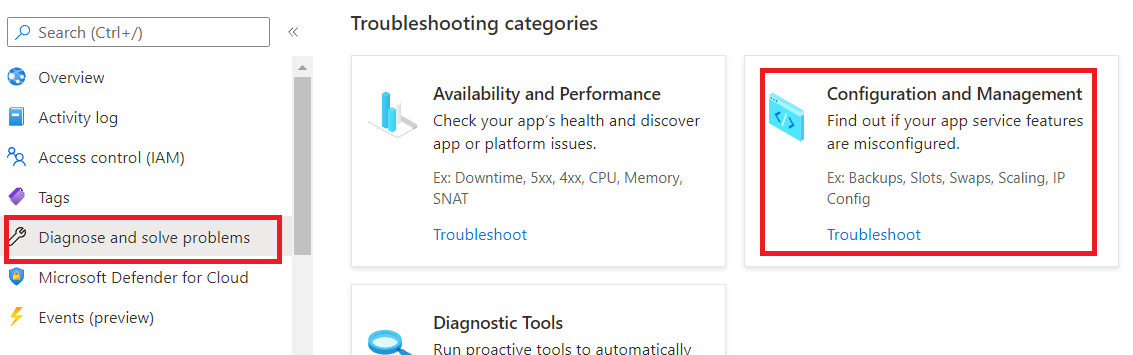
- Go to “Diagnose and Solve problems” sub menu and click on “Configuration Management”
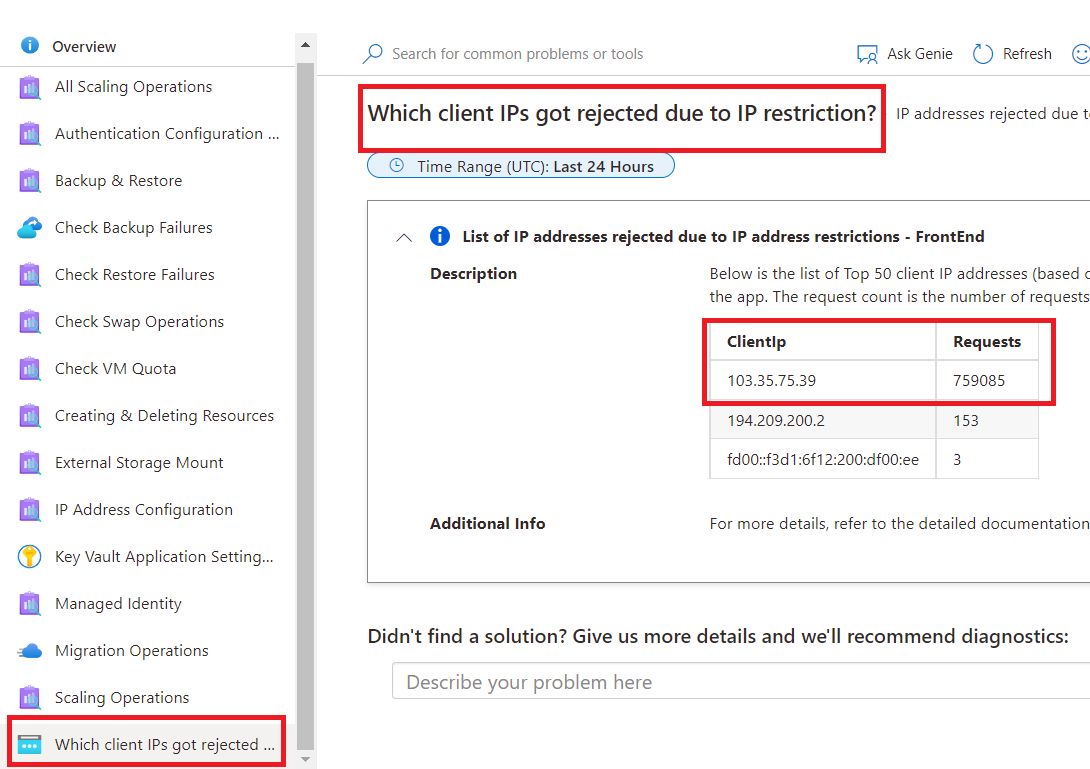
- Then click on the option at the bottom labeled “Which client IPs got rejected due to IP restriction?”
- Finally you’ll have your answer, a table showing the top rejected ips with the number of accesses.
- Go back to your Networking “Access Restrictions” rules and change “the allow rule” you had to your ip to deny and use the IP at the top of table
- Also don’t forget to add a new “allow all” rule using ip address 0.0.0.0 with a higher priotiry than your deny rules
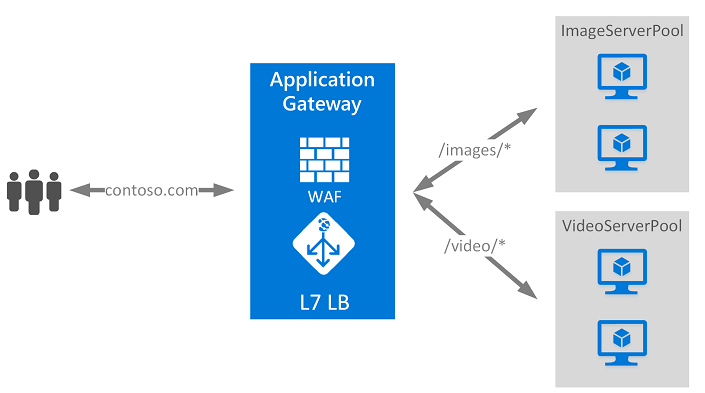
There are obviously other ways and better ways to protect against DDoS like having an “Application Gateway” to control acesses to your Web App but has higher costs and requires further customization, the goal here was an easy way to find clients IP accessing your Azure Web App Linux.