A recent blog post explaining how to identify which users/devices are still using Basic Authentication took off on Reddit and there were several comments asking how to handle the legacy clients. So we decided to document a few suggestions on how to move legacy clients into Modern Authentication.
These are the most common devices on Basic Authentication:
- Users using old email clients or not properly configured (like iPhone/iOS)
- Scanners/Printers using SMTP
- Software which sends email through legacy protocols, can be: CRM, sending Newsletters, Marketing campaigns,etc
- Migrate to Modern Authentication Office/Outlook 2013
- Migrate to Modern Authentication Teams Rooms devices
- How to block future sign-ins from using basic authentication to test migrated devices ?
Below is a straight to the point list on how to handle each of these scenarios, we also have a Web App which will monitor for legacy clients and will notify you whenever one connects:
How can I move users with iPhone or macOS to Modern Authentication
Update July 26th: Microsoft probably realised the amount of support requests they would get from iOS users which are still using Exchange ActiveSync through Basic Authentication. With Apple’s help they’ve launched a small fix which will move the devices automatically to Modern Authentication (OAauth) as long as the devices are running the latest iOS 15.6/macOS Monterey 12.0 and tenant admins follow these steps.
- First, all iPhones must be running at least iOS 15.6 (launched July 20th)
- Second, the iOS Accounts App must have tenant wide permission given by Admins, so it can exchange the user password for an OAuth token.
- To provide the required permissions, access this link using an admin account and grant access to all tenant.
To confirm everything worked open Azure AD -> Enterprise Applications -> All applications page and search for “iOS Accounts” (also check “Apple Internet Accounts”).
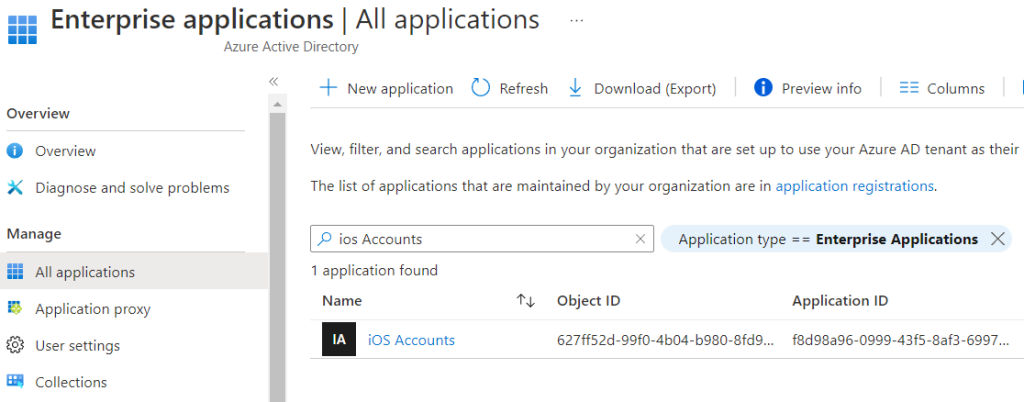
Click on the App entry and on the left side click “Permissions” and make sure you have granted consent, otherwise click the Blue Button “Grant Admin consent”. Please note the blue button will always be there even after you’ve granted permissions
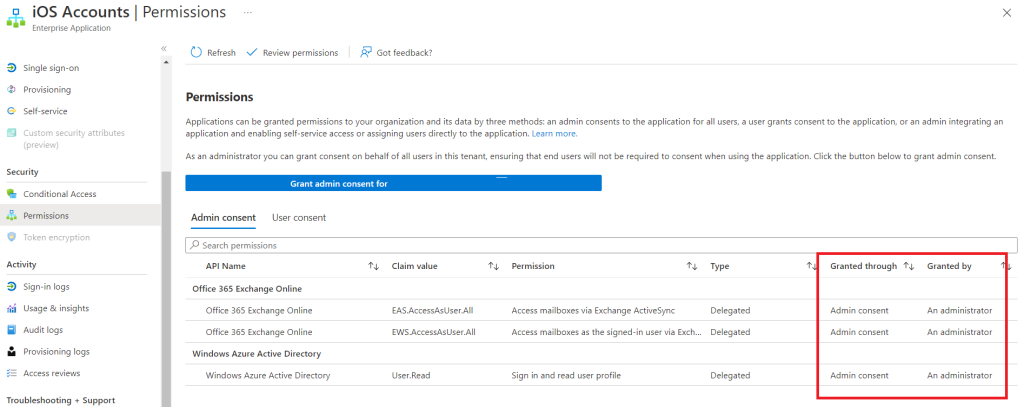
That’s it, next time the devices connect they should automatically migrate themselves to Modern Authentication (OAuth). Use our Web App which monitors daily for new Basic Authentication devices and receive a notification to make sure coming October there aren’t legacy protocols still running.
More details on Microsoft blog post about the iOS 15.6 update
The other option for devices not running the required iOS versions is to Remove and Re-add the account by selecting “Sign In” and not “Configure Manually”.
Just a note of caution, when removing the email account we had users loosing some of their contacts because they were being synced with Exchange and when we re-added the account most of the time they would come back, but in some situations they didn’t, so we recommend making sure Contacts are backed up.
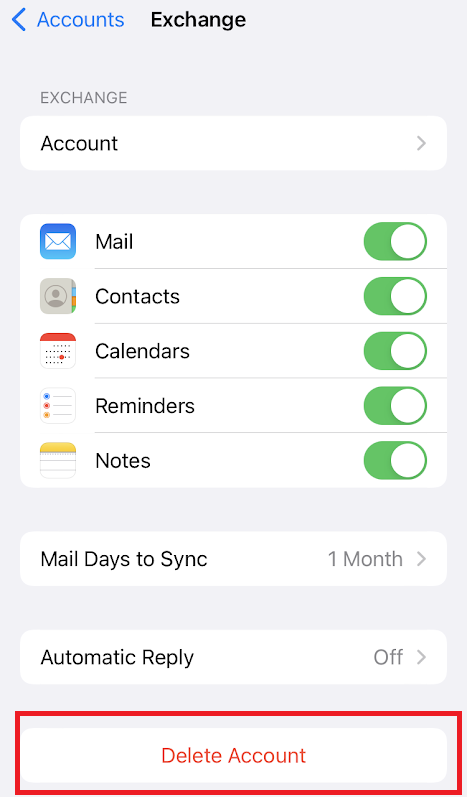
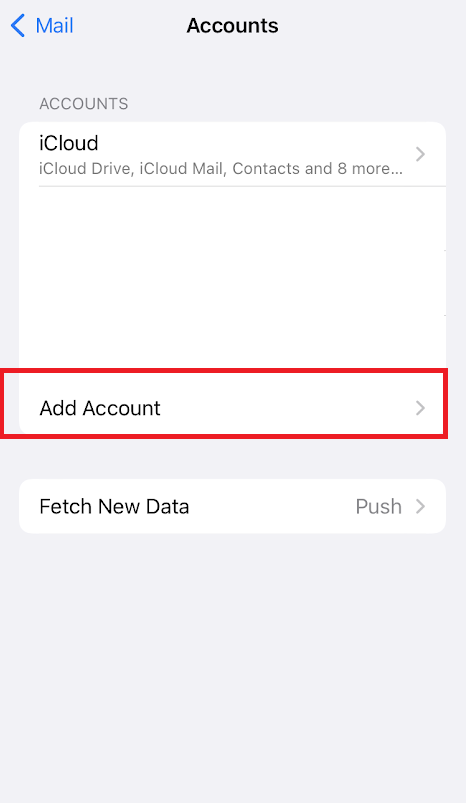

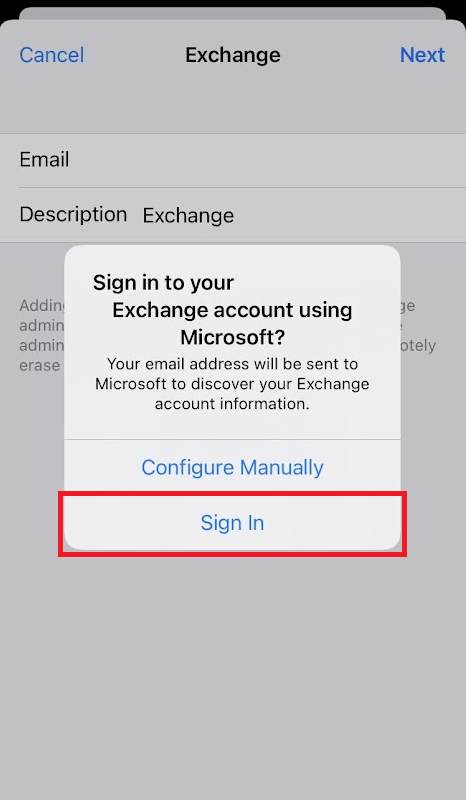
My tenant sign-in logs still show a lot of iPhone/iPad using Basic Authentication after applying these steps
The main reason for this is that although the tenant has granted wide authorization for the iOS Mail App backend to exchange credentials (Basic Auth) for OAauth token (Modern Authentication) the devices aren’t running at least iOS 15.6.
So, how can admins know which version of iOS are devices running on the tenant ?, this information comes mainly from the “User Agent” data on the sign-in logs which might not be simple to interpret but using our Web App you’ll be able to know the iOS version plus what to do.
I have devices (scanners, printers, etc) sending emails through SMTP connection with Exchange Online
On this subject Microsoft decided, for now, not to force Modern Authentication: “SMTP AUTH will still be available when Basic authentication is permanently disabled on October 1, 2022”
As long as you were using it before the deadline, you’ll be able to keep using afterwards. There are just a few things you need to check:
- Your device must be compatible with TSL 1.2 or above: This means you must enable TLS/StartTLS option, the connection port can be either 587 (better) or 25.
If you only have port 465 as an option, it won’t work.

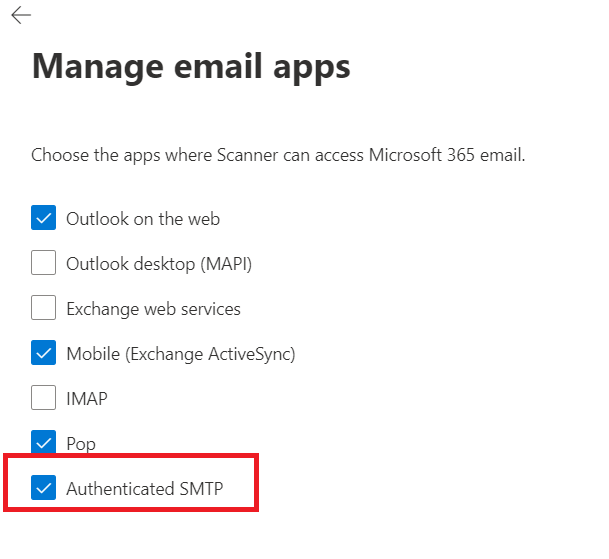
I’m using a third party software which connects to our mailboxes using legacy protocols (IMAP, POP3, SMTP)
You’ll need to change how the software connects to your tenant by authenticating the connection through OAuth
This basically means using Microsoft Graph API to retrieve and send email with the help of an authentication token. Using OAuth is not hard, but it will require development or at least selecting this authentication option on your third party software
The required permission levels and a guide on how to do POP3,SMTP and IMAP through OAuth can be found on Microsoft Documentation.
How to enable Modern Authentication on Office/Outlook 2013
By default Office 2013 (including Outlook 2013) will connect using Basic Authentication so in order to migrate to Modern Authentication a few Windows Registry entries must be changed:
- Create a REG_DWORD entry on
HKEY_CURRENT_USER\Software\Microsoft\Exchange\AlwaysUseMSOAuthForAutoDiscoverwith value1 - Create a REG_DWORD entry on
HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\Identity\EnableADALwith value1 - Create a REG_DWORD entry on
HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\Identity\Versionwith value1
“If you’re currently signed in to any of Office client apps, you need to sign out and sign back in for the change to take effect.”
Move Teams Room to Modern Authentication
Through the device settings:
- On Microsoft Teams Rooms, go to More (…).
- Select Settings, and then enter the device administrator username and password.
- Go to the Account tab, turn on Modern Authentication, and then select Save and exit.
